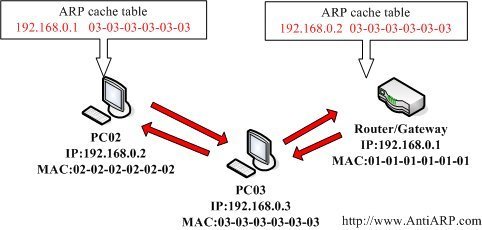
1. Lan card ada 2
2. Alokasi IP address pada Mikrotik Hotspot Gateway :
- to_hotspot ip public
- to_hotspot 10.10.0.1/16
/ip firewall filter add chain=block-forward action=accept protocol=icmp icmp-options=8:0 limit=1,0 comment=”Allow ICMP”
/ip
firewall filter add chain=block-forward action=log tcp-flags=syn
protocol=tcp limit=5/1m,0 log-prefix=”Firewalled packet:” comment=”# Log
Forward”
/ip
firewall filter add chain=block-forward action=log protocol=icmp
icmp-options=8:0 limit=10/1h,0 log-prefix=”PING of Death ???” comment=”#
Log PING of Death”
/ip firewall filter add chain=block-forward action=drop src-address=169.254.0.0/16 comment=”# Block bad IP address”
/ip firewall filter add chain=block-forward action=drop src-address=224.0.0.0/3
/ip firewall filter add chain=block-forward action=drop src-address=224.0.0.0/4
/ip firewall filter add chain=block-forward action=drop src-address=240.0.0.0/5
/ip firewall filter add chain=block-forward action=drop src-address=248.0.0.0/5
/ip firewall filter add chain=block-forward action=drop src-address=255.255.255.255
/ip firewall filter add chain=block-forward action=drop connection-state=invalid comment=”# Drop invalid connections”
/ip firewall filter add chain=block-input action=accept protocol=icmp icmp-options=8:0 limit=5,0 comment=”# Allow ICMP”
/ip
firewall filter add chain=block-input action=log protocol=icmp
icmp-options=8:0 limit=10/1h,0 log-prefix=”PING of Death ???” comment=”#
Log PING of Death”
/ip
firewall filter add chain=block-input action=log tcp-flags=syn
protocol=tcp limit=5/1m,0 log-prefix=”Firewalled packet:” comment=”# Log
input”
/ip firewall filter add chain=block-input action=drop protocol=icmp comment=”# Block PING of Death”
/ip
firewall filter add chain=block-input action=drop
in-interface=to_internet src-address=10.0.0.0/8 comment=”# Interface
facing Public Internet Inbound Section RFC 1918″
/ip firewall filter add chain=block-input action=drop in-interface=to_internet src-address=202.91.11.6
/ip firewall filter add chain=block-input action=drop in-interface=to_internet src-address=192.168.0.0/16
/ip firewall filter add chain=block-input action=drop in-interface=to_internet src-address=202.91.8.160/29
/ip firewall filter add chain=block-input action=drop src-address=0.0.0.0/8
/ip firewall filter add chain=input action=jump jump-target=block-input comment=”# Jump to block-input”
/ip firewall filter add chain=forward action=jump jump-target=block-forward comment=”# Jump to block-forward”
/ip firewall filter add chain=forward action=jump jump-target=block-ddos protocol=udp comment=”# Jump to block-ddos”
/ip firewall filter add chain=forward action=jump jump-target=block-service comment=”# Jump to block-service”
/ip
firewall filter add chain=block-service action=drop p2p=all-p2p
comment=”# Block ports you don’t want it insert here ..:: drop p2p ::..”
/ip
firewall filter add chain=block-service action=drop
out-interface=to_internet dst-port=5050 protocol=tcp comment=”..:: drop
yahoo messenger ::..”
/ip
firewall filter add chain=block-service action=drop
out-interface=to_internet dst-port=6666-7000 protocol=tcp comment=”..::
drop irc ::..”
/ip firewall filter add chain=block-input action=drop src-address=127.0.0.0/8
/ip firewall filter add chain=block-input action=drop src-address=169.254.0.0/16
/ip firewall filter add chain=block-input action=drop src-address=172.16.0.0/12
/ip firewall filter add chain=block-input action=drop src-address=192.0.2.0/24
/ip firewall filter add chain=block-input action=drop src-address=204.152.64.0/23
/ip firewall filter add chain=block-input action=drop src-address=224.0.0.0/3
/ip firewall filter add chain=block-input action=drop src-address=224.0.0.0/4
/ip firewall filter add chain=block-input action=drop src-address=240.0.0.0/5
/ip firewall filter add chain=block-input action=drop src-address=248.0.0.0/5
/ip firewall filter add chain=block-input action=drop src-address=255.255.255.255
/ip
firewall filter add chain=block-input action=drop
in-interface=to_internet src-address=202.91.8.167 comment=”# Block Smurf
Attack on all interface”
/ip firewall filter add chain=block-input action=drop in-interface=to_internet src-address=202.91.11.7
/ip firewall filter add chain=block-input action=drop in-interface=to_hotspot src-address=10.10.255.255
/ip firewall filter add chain=block-input action=drop in-interface=to_proxy src-address=192.168.100.255
/ip firewall filter add chain=block-input action=drop dst-port=113 protocol=tcp comment=”# Block Ident”
/ip firewall filter add chain=block-input action=drop fragment=yes comment=”# Block IP Frags”
/ip
firewall filter add chain=block-input action=drop
ipv4-options=loose-source-routing comment=”# Blocked source routed
packets lsrr and ssrr”
/ip firewall filter add chain=block-input action=drop ipv4-options=strict-source-routing
/ip
firewall filter add chain=block-input action=reject
reject-with=tcp-reset in-interface=to_internet dst-port=80 protocol=tcp
comment=”# Reject connection from internet to port 80”
/ip
firewall filter add chain=block-forward action=reject
reject-with=tcp-reset tcp-flags=syn,ack connection-state=new
protocol=tcp comment=”# Reject Bad TCP”
/ip firewall filter add chain=block-forward action=drop protocol=icmp comment=”# Block PING of Death”
/ip
firewall filter add chain=block-input action=drop
in-interface=to_internet dst-port=23 protocol=tcp comment=”# Block
Telnet come from Internet”
/ip
firewall filter add chain=block-input action=drop
in-interface=to_hotspot dst-port=23 protocol=tcp comment=”# Block Telnet
come from Hotspot”
/ip firewall filter add chain=block-forward action=drop dst-port=137-139 protocol=tcp comment=”# Block Netbios Sessions tcp”
/ip firewall filter add chain=block-input action=drop dst-port=137-139 protocol=tcp comment=”# Block Netbios Sessions tcp”
/ip firewall filter add chain=block-input action=drop dst-port=137-139 protocol=udp comment=”# Block Netbios Sessions udp”
/ip firewall filter add chain=block-forward action=drop dst-port=135-139 protocol=udp comment=”# Block Netbios Sessions udp”
/ip firewall filter add chain=block-ddos action=return limit=16,32
/ip firewall filter add chain=block-ddos action=log log-prefix=”DDOS ATTACK:”
/ip firewall filter add chain=block-ddos action=drop limit=16,32
/ip firewall filter add chain=input action=jump jump-target=block-ddos protocol=udp comment=”# Jump to block-ddos”
/ip
firewall filter add chain=tcp-flags action=jump jump-target=bad-flags
tcp-flags=fin,!ack protocol=tcp comment=”# tcp-flags jumpt to bad-flags”
/ip firewall filter add chain=tcp-flags action=jump jump-target=bad-flags tcp-flags=psh,!ack protocol=tcp
/ip firewall filter add chain=tcp-flags action=jump jump-target=bad-flags tcp-flags=urg,!ack protocol=tcp
/ip firewall filter add chain=tcp-flags action=jump jump-target=bad-flags tcp-flags=fin,rst protocol=tcp
/ip firewall filter add chain=tcp-flags action=jump jump-target=bad-flags tcp-flags=fin,syn protocol=tcp
/ip firewall filter add chain=tcp-flags action=jump jump-target=bad-flags tcp-flags=syn,rst protocol=tcp
/ip firewall filter add chain=tcp-flags action=jump jump-target=bad-flags tcp-flags=fin,syn,rst,psh,ack,urg,ece,cwr protocol=tcp
/ip
firewall filter add chain=tcp-flags protocol=tcp action=jump
jump-target=bad-flags tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg,!ece,!cwr
/ip
firewall filter add chain=tcp-flags protocol=tcp action=jump
jump-target=bad-flags tcp-flags=fin,psh,urg,!syn,!rst,!ack,!ece,!cwr
/ip
firewall filter add chain=tcp-flags action=jump jump-target=bad-flags
tcp-flags=fin,syn,psh,urg,!rst,!ack,!ece,!cwr protocol=tcp
/ip
firewall filter add chain=tcp-flags action=jump jump-target=bad-flags
tcp-flags=fin,syn,rst,ack,urg,!psh,!ece,!cwr protocol=tcp
/ip firewall filter add chain=input action=jump jump-target=tcp-flags protocol=tcp comment=”# Jump to tcp-flags”
/ip firewall filter add chain=bad-flags action=log log-prefix=”TCP BAD FLAGS:”
/ip firewall filter add chain=bad-flags action=drop
/ip firewall filter add chain=syn-flood action=return tcp-flags=syn,!fin,!rst,!ack protocol=tcp limit=5,10
/ip firewall filter add chain=syn-flood action=return protocol=!tcp
/ip firewall filter add chain=syn-flood action=return tcp-flags=!,syn,!fin,!rst,!ack protocol=tcp
/ip firewall filter add chain=syn-flood action=log log-prefix=”SYN FLOOD:”
/ip firewall filter add chain=syn-flood action=drop
/ip
firewall filter add chain=input action=jump jump-target=syn-flood
tcp-flags=syn,!fin,!rst,!ack protocol=tcp comment=”# Jump to syn-flood”
/ip firewall filter add chain=block-forward action=drop dst-port=445 protocol=tcp comment=”# Block CIFS tcp”
/ip firewall filter add chain=block-forward action=drop dst-port=135 protocol=tcp comment=”# Block RPC Portmapper”
/ip firewall filter add chain=block-forward action=drop dst-port=135 protocol=udp
/ip firewall filter add chain=block-forward action=drop dst-port=111 protocol=tcp
/ip firewall filter add chain=block-input action=drop dst-port=135 protocol=tcp comment=”# Block RPC Portmapper”
/ip firewall filter add chain=block-input action=drop dst-port=135 protocol=udp
/ip firewall filter add chain=block-input action=drop dst-port=111 protocol=tcp
/ip firewall filter add chain=block-input action=drop dst-port=111 protocol=udp
/ip firewall filter add chain=block-input action=drop dst-port=445 protocol=tcp comment=”# Block CIFS tcp”
/ip firewall filter add chain=block-forward action=drop dst-port=111 protocol=udp
/ip firewall filter add chain=block-forward action=drop dst-port=69 protocol=tcp comment=”# Block TFTP”
/ip firewall filter add chain=block-input action=drop dst-port=69 protocol=tcp comment=”# Block TFTP”
/ip firewall filter add chain=block-input action=drop dst-port=69 protocol=udp
/ip firewall filter add chain=block-input action=drop dst-port=20034 protocol=tcp comment=”# Block Netbus”
/ip firewall filter add chain=block-input action=drop dst-port=20034 protocol=udp
/ip firewall filter add chain=block-input action=drop dst-port=3133 protocol=tcp comment=”# Block Back0riffice”
/ip firewall filter add chain=block-input action=drop dst-port=3133 protocol=udp
/ip firewall filter add chain=block-forward action=drop dst-port=69 protocol=udp
/ip firewall filter add chain=block-forward action=drop dst-port=20034 protocol=tcp comment=”# Block Netbus”
/ip firewall filter add chain=block-forward action=drop dst-port=20034 protocol=udp
/ip firewall filter add chain=block-forward action=drop dst-port=3133 protocol=tcp comment=”# Block Back0riffice”
/ip firewall filter add chain=block-forward action=drop dst-port=3133 protocol=udp
/ip firewall filter add chain=block-input action=drop dst-port=2049 protocol=udp comment=”# Block NFS”
/ip firewall filter add chain=block-input action=drop dst-port=2049 protocol=tcp
/ip firewall filter add chain=block-forward action=drop dst-port=2049 protocol=udp comment=”# Block NFS”
/ip firewall filter add chain=block-forward action=drop dst-port=2049 protocol=tcp
/ip
firewall filter add chain=block-service action=drop
out-interface=to_internet dst-port=1818 protocol=tcp comment=”# Block
Game online”
/ip firewall filter add chain=block-service action=drop out-interface=to_internet dst-port=6112 protocol=tcp